Infrastructure
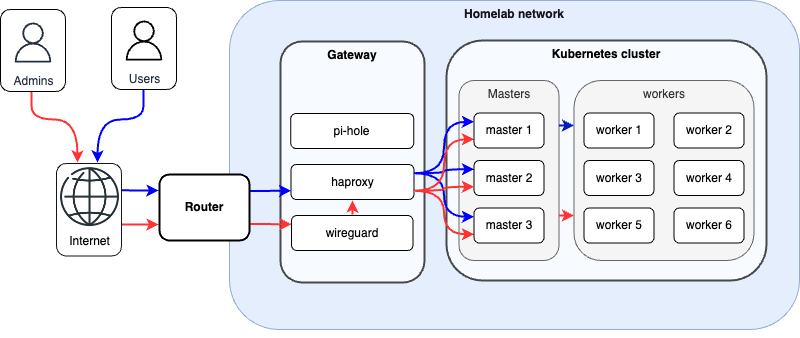
Gateway
A host is configured as the gateway to the local network (i.e handle all incoming traffic). It runs various services deployed with systemd :
- Haproxy for loadbalancing all incoming external requests (ports 80 & 443) to the k3s cluster and loadbalancing k3s api server (port 6443).
- PiHole (optional) for advertisements filtering.
- Wireguard (optional) for external access to the local network (i.e from internet). VPN clients could be add using the web interface (see. services section).
K3S cluster
Some hosts are configrured to run k3s (Lightweight Kubernetes) with the following roles :
- 3 x master nodes
- 5 x worker nodes
The cluster comes with k3s integrated klipper loadbalancer (traefik ingressController is disabled and installed manually). For convenience, system-upgrade-controller is deployed to perform an automatic k3s upgrade on each node by using two plans (one for masters and the other one for workers).
Longhorn is used to deliver distributed block storage accross kubernetes, it will enroll all servers tagged additional_disk: true in inventory/hosts.yml.